For the past few weeks a lot has been spoken, written and talked about is GDPR Compliance. I have always retained the view that Europeans are much more intelligent when it comes to compliance and regulatory of Personal Data then Americans. I am not going to use the word privacy because its been the most mocked around word in some quarters and of course in USA we all know how well its protected and implemented. 😀
I’ll start with first highlighting some key aspects of GDPR – like
- What is GDPR
- Key Regulatory Requirements
- Role of IT Professionals
- Actions for Compliance (12 Steps)
- Microsoft and GDPR (Compliance Manager and Azure Information Protection Scanner)
- GDPR Templates
What is GDPR
Its not something new and before GDPR we had Data Protection Act so if you had it implemented then you will go through less pain since a lot of elements are partially covered by it. The whole idea and concept is to know how the data is collected, where the data resides, stored, processed, deleted, who can access it and how its used for EU citizens. This means that organizations will be required to show the data flow or lifecycle to minimize any risk of personal data being leaked and all required steps are in place under GDPR.
In short, GDPR is to have common sense data security ideas, especially from the Privacy by Design school of thought: minimize collection of personal data, delete personal data that’s no longer necessary, restrict access, and secure data through its entire lifecycle and also by adding requirements for documenting IT procedures, performing risk assessments under certain conditions, notifying the consumer and authorities when there is a breach, as well as strengthening rules for data minimization.
Key Regulatory Requirements
PRIVACY BY DESIGN

PbD is referenced heavily in Article 25 of the GDPR, and in many other places in the new regulation. It’s not too much of a stretch to say that if you implement PbD, you’re well on your way to successfully implement the GDPR. Privacy by Design (PbD) has always played a part in EU data regulations. But with the new law, its principles of minimizing data collection and retention and gaining consent from consumers when processing data are more explicitly formalized. The idea is to minimize collection of consumer data, minimize who you share the data with, and minimize how long you keep it. Less is more: less data for the hacker to take, means a more secure environment. So the data points you collected from a web campaign over three years ago — maybe containing 15000 email addresses along with favourite pet names — and now lives in a spreadsheet no one ever looks at. Well, you should find it and delete it.If a hacker gets hold of it, and uses it for phishing purposes, you’ve created a security risk for your customers. Plus, if the local EU authority can trace the breach back to your company, you can face heavy fines.
DATA PROTECTION IMPACT ASSESSMENT
Data Protection Impact Assessments: When certain data associated with subjects is to be processed, companies will have to first analyze the risks to their privacy. This is another new requirement in the regulation. You may also need to run a DPIA if the nature, scope, context, and purposes of your data processing place high risk to the people’s rights and freedoms. If so, before data processing can commence, the controller must produce an assessment of the impact on the protection of personal data.
Who exactly determines whether your organization’s processing presents a high risk to the individuals’ rights and freedoms? The text of the GDPR is not specific, so each organization will have to decide for itself.
RIGHT TO ERASE AND TO BE FORGOTTEN
Discussed in Article 17 of the GDPR, it states that “The data subject shall have the right to obtain from the controller the erasure of personal data concerning him or her without undue delay and the controller shall have the obligation to erase personal data without undue delay where … the personal data are no longer necessary in relation to the purposes for which they were collected or otherwise processed; … the data subject withdraws consent on which the processing is based … the controller has made the personal data public and is obliged … to erase the personal data”. There’s been a long standing requirement in the DPD allowing consumers to request that their data be deleted. The GDPR extends this right to include data published on the web.

is the still controversial right to stay out of the public view and “be forgotten”. This means that in the case of a social media service that publishes personal data of a subscriber to the Web, they would have to remove not only the initial information, but also contact other web sites that may have copied the information. This would not be an easy process!
EXTRATERRITORIAL
The new principle of extraterritoriality in the GDPR says that even if a company doesn’t have a physical presence in the EU but collects data about EU data subjects — for example, through a web site—then all the requirements of GDPR are in effect. In other words, the new law will extend outside the EU. This will especially affect e-commerce companies and other cloud businesses.

It also means that data controllers are regulated by a lead data protection authority located in the territory of their main establishment. The European Commission has the power to decide if a country outside the EEA provides adequate protection and declare “a territory or one or more specified sectors within that country” adequate. For example, although the United States is not deemed to be an “adequate” jurisdiction, as of 1 August 2016, organisations located in the U.S. may register with the EU-U.S. Privacy Shield. Legal experts note this may not be that easy to enforce and extraterritoriality is particularly relevant to core web services such as search, social networking, e-commerce, companies that allow you to rent apartments online, etc.
BREACH NOTIFICATION
Breach Notification: A new requirement not in the existing DPD is that companies will have to notify data authorities within 72 hours after a breach of personal data has been discovered. Data subjects will also have to be notified but only if the data poses a “high risk to their rights and freedoms”. According to Article 33 breaches can be categorized according to the following security principles:
– Confidentiality breach – where there is an unauthorized or accidental disclosure of, or access to, personal data.

– Integrity breach – where there is an unauthorized or accidental alteration of personal data.
– Availability breach – where there is an accidental or unauthorized loss of access to, or destruction of, personal data (include where data has been deleted either accidentally or by an unauthorized person).
- Fines: The GDPR has a tiered penalty structure that will take a large bite out of offender’s funds. More serious infringements can merit a fine of up to 4% of a company’s global revenue. This can include violations of basic principles related to data security — especially PbD principles. A lesser fine of up to 2% of global revenue — still enormous — can be issued if company records are not in order or a supervising authority and data subjects are not notified after a breach. This makes breach notification oversights a serious and expensive offense.
Role of IT Professionals
Information Security today is just not limited to the IT Department of any organization and as businesses have evolved during time, so does the need for everyone in the business for making his or her contribution to the security of the organisation’s information, and for protecting the personal data the organisation uses. You will notice that most GDPR webinars are attended by business managers, compliance people and the like and these people are responsible for operating and overseeing GDPR compliance. Asking colleagues what data they hold, and getting the company lawyer to update standard contract terms and write privacy notices. But they can’t really do all this stuff on their own since they need IT for doing most of the work like providing a dump of the database schema, gives a guranteed correct version and don’t forget the unique access required to scan the various files stored in local hard disks and networked file shares for the millions of files we use in the form of documents, emails, spreadsheets, meeting notes, etc.
It is extremely important to engage the IT Team from the discovery phase and don’t forget subject access requests (SARs), for example: most of us hardly ever had one because nobody’s really been sufficiently bothered to spend the money and ask what data you hold about them. The other thing you need to understand is whether there’s a gap between how you think you work and how you actually work. For example backups:
even though your backup strategy is documented, do you really understand how it’s implemented by the tech teams? How your disk-to-disk-to-tape setup really works? Who transports the tapes to offsite storage? Do you destroy tapes when you say you will? If you’ve erased someone’s data on request, does the tech team re-delete the data from the live system if they’ve had to restore from backup?
Nearly everyone organization i have come across keeps some sort of back up with them and not everyone is fully utilizing the Cloud infrastructure and Back up tools. The data aspect is important and becoming compliant is one thing, but being able to quantify compliance is quite another. Anyone who’s read BS 10012 (Data protection – Specification for a personal information management system) will be familiar with clause 9.1, which is all about “monitoring, measurement, analysis and evaluation”.
Now i am not a lawyer but just to give you some insight on how tricky things can get i am listing down a couple of items which might be eye opener for some of you. I wasn’t able to get a clear cut answer about these from anyone and could not find any details in GDPR or the hundreds of lawyer websites claiming to make you compliant with GDPR in just weeks.
For example how can a small company which runs its site on PHP and have a user forum implement GDPR? It can be very time consuming for them and some key aspects are tricky to be implemented.
– Any web community will at least be storing usernames, passwords, emails and most likely IP addresses. As far as I know, all of that counts and comes under PID (Personal Identifiable Data)
One can say that you’re allowed to log people’s IP addresses for diagnostic reasons, to prevent fraud and abuse. You don’t have to delete these logs when someone emails you if they’re still useful for those purposes. You do need to delete those logs eventually though, and you need to disclose how often that is. It can be ten years if you want. Yeah but where does it say this and who decides?
– What happens when i restore the backup?
Now all old usernames, emails and ip addresses will be part of the system again and how do i delete it them or keep track of them 🙂 Yup you need to define a solid process for this .
Of course if you’re Facebook or Twitter you just assign a few developers to this and you’ll be fine. But this might affect small-time web companies.
Actions for Compliance
Below is a list of Actions the organization needs to take in order to comply with GDPR and the timeline is mostly representing implementation for a medium to large size organization.
Step 1 – Data Mapping

3 to 6 Months
ACTIONS
Identify and map your data processing activities, including data flows and use cases in order to create a comprehensive record of activities.
WHY?
GDPR requires you to keep detailed records of data processing activities. These records can be used to assess the compliance steps required by the business going forward and respond quickly to data breaches and to individuals who request their own data.
STEP 2 – Privacy Governance / Data Protection

1 – 3 Months
ACTION
Assess whether you are required to appoint a Data Protection Officer (DPO) and if so, recruit a professional who meets the GDPR criteria. Irrespective of the legal requirement, review and, if necessary, improve the corporate governance policies and structure to ensure that they are effective to achieve reasonable compliance throughout the business.
WHY?
Appointment of a DPO is mandatory for some businesses. Robust data governance is, in any event, key to fulfilling the accountability obligation of all organizations.
STEP 3 – Data Sharing

2 – 6 Months
ACTION
Identify any data sharing with third parties, determine the role of those parties and put appropriate safeguards in place. This may require the execution of new or revision of existing agreements.
WHY?
GDPR imposes mandatory content for certain agreements and requires the clear assignment of roles and responsibilities.
STEP 4 – Justification of Processing

2 – 6 Months
ACTION
Review or establish legal bases for processing, at least for key use cases. Plan and implement remedial action to fill any compliance gaps.
WHY?
GDPR requires that all data processing has a legal basis, such as consent, contract and balance of interests, etc. and makes usage more difficult. GDPR also contains restrictions / additional obligations relating to the use of automated processing, including profiling.
STEP 5 – Privacy Notices and Consents

2 – 3 Months
ACTION
Review and amend all privacy notices, consent forms and related processes in order to comply with the GDPR.
WHY?
The GDPR imposes additional minimum consent for privacy notices. It also imposes stricter consent requirements.
STEP 6 – Data Protection Impact Assessment

1 – 3 Months
ACTION
Assess whether the business carries out any “high risk” processing under the GDPR. If so, carry out a Data Protection Impact Assessment (DPIA) and, if necessary, consult with your supervisory authority.
WHY?
DPIAs must be carried out in relation to all “high risk” processing and consultation with supervisory authorities may be required in certain circumstances.
STEP 7 – Policies

2 – 6 Months
ACTION
Review and supplement the company’s existing suite of polices and processes dealing with data protection, including those dealing with data retention and integrity, such as data accuracy and relevance.
WHY?
The GDPR imposes stricter obligations to keep data accurate, proportionate and no longer than necessary.
STEP 8 – Individual Rights

1 – 3 Months
ACTION
Identify the new individual rights provided by the GDPR and establish procedures for dealing with them. Review the procedures in place in order to comply with existing rights and set up any new internal procedures and processes, where required.
WHY?
GDPR extends existing rights and introduces new rights for individuals, such as the right of data portability.
STEP 9 – Data, Quality, Privacy by Design and Default

6 – 9 Months
ACTION
Review or establish procedures for ensuring that GDPR compliance is embedded in all applications and processes that involve personal data from the start. Default settings must comply with the GDPR.
WHY?
Compliance must be integrated into all processes and applications that involve the use of personal data, and default settings must comply with the GDPR, including data minimization.
STEP 10 – International Data Transfers

2 – 3 Months
ACTION
Identify and review the data transfer mechanisms in place in order to comply with the GDPR. Fill any gaps, including entering into Standard Contractual Clauses with service providers and group companies, and evaluate the use of Binding Corporate Rules (“BCRs”).
WHY?
The GDPR retains the current requirement to have adequate measures in place when transferring personal data outside the EEA, but sanctions for non-compliance are substantially increased.
STEP 11 – Data Security & Breach Management Process

3 – 6 Months
ACTION
Review the data security measures in place to ensure they are sufficient and to assess whether the specific measures referred to in the GDPR are (or should be) in place. Review or establish an effective Data Breach Response Plan.
WHY?
The GDPR implements stricter requirements regarding appropriate technical and organizational data security measures. It also requires data breaches involving risk to individuals to be reported to supervisory authorities without delay and within 72 hours (unless a longer period can be justified); affected individuals must also be notified if the breach is high risk.
STEP 12 – Roll out of Compliance Tools & Staff Training

2 – 6 Months
ACTION
Roll-out amended and new privacy notices and consent forms. Publish new and revised policies and procedures and conduct training of key personnel on GDPR compliance.
Microsoft and GDPR
Microsoft provides two great compliance solutions which can really help organizations assess and manage compliance risks:
Compliance Manager: A single pane of glass with ongoing risk assessment on Microsoft cloud services, actionable insights, and recommended actions to improve data protection capabilities, as well as simplified compliance via streamlined workflow and audit-ready reports. Compliance Manager is a cross-Microsoft Cloud services solution designed to meet complex compliance obligations, including the EU GDPR, ISO 27001, ISO 27018, NIST 800- 53, NIST 800- 171, and HIPAA. It also provides you the information and tools to conduct self-assessment for your responsibilities of meeting regulatory requirements. Compliance Score is a new feature for Compliance Manager which gives you visibility into your organization’s compliance stature with a risk-based score reference.
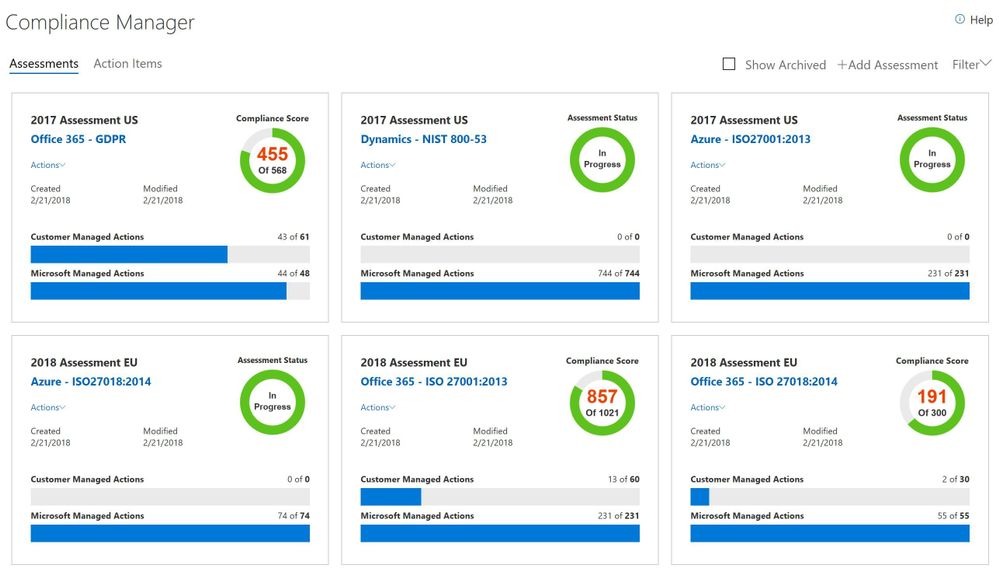
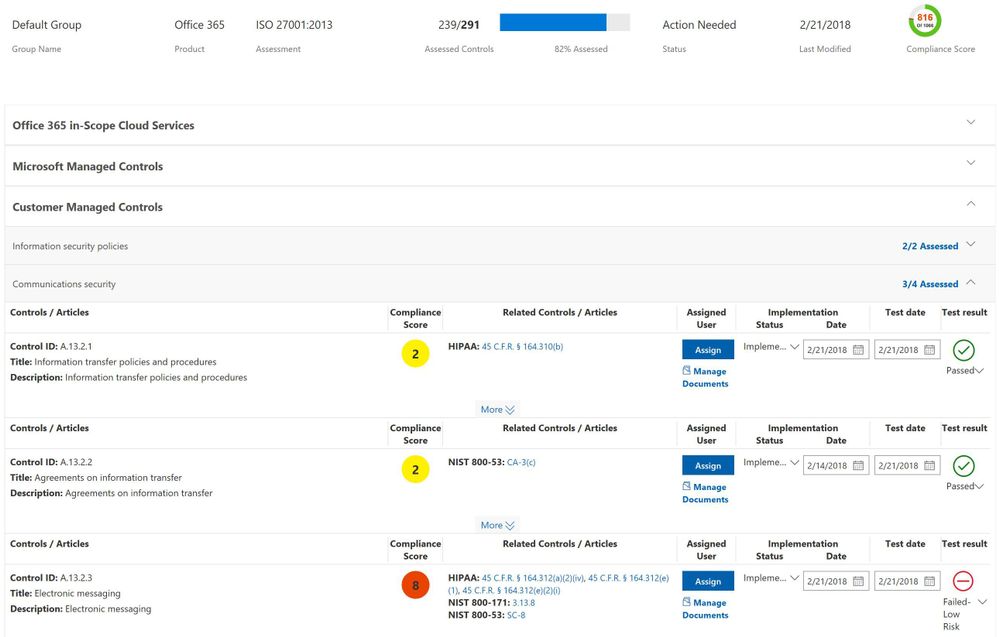
By using group functionality, you can now create multiple assessments for any standard or regulation that is available to you in Compliance Manager by time, by teams, or by business units. For example, you can create a GDPR assessment for the 2018 group and another one for the 2019 group. Similarly, you can create an ISO 27001 assessment for your business units located in the U.S. and another one for your business units located in Europe. This functionality gives you a more robust way to manage compliance activities based on your organizational needs for performing risk assessments.
Azure Information Protection Scanner: It lets you configure policies to automatically discover, classify, label, and protect documents in on-premises repositories like file servers and on-premises SharePoint servers. The classification is identifiable always, regardless of where the data is stored or with whom it’s shared. The labels include visual markings such as a header, footer, or watermark. Metadata is added to files and email headers in clear text. The clear text ensures that other services, such as data loss prevention solutions, can identify the classification and take appropriate action.
The following are the licenses and what is supported for each:
- Azure Information Protection P2: Support for all classification, labeling, and protection features.
- Azure Information Protection P1: Support for most classification, labeling, and protection features, but not automatic classification or Hold Your Own Key (HYOK).
- Office 365 that includes the Azure Rights Management Service: Support for protection but not classification and labeling.
‘Azure Information Protection‘ document and email protections are handled via ‘Azure Rights Management‘. This protection technology uses encryption, identity, and authorization policies. Similarly, to the labels that are applied, protection that is applied by using Rights Management stays with the documents and emails, independently of the location—inside or outside your organization, networks, file servers, and applications. This information protection solution keeps you in control of your data, even when it is shared with other people.
one of the first tasks in a GDPR exercise is to know and find the content you have and then classify as needed. This can often be the biggest problem, as most organizations have content stored in collaboration tools such as SharePoint, file servers, local machines or other applications. Asking business users to go to these locations and classify is a task that will never happen.
the scanner is a separate download using the following URL, but in the future, it will be bundled as part of the ‘Azure Information Protection‘ client.
https://www.microsoft.com/en-us/download/details.aspx?id=53018
From the download select the ‘AzInfoProtectionScanner’.
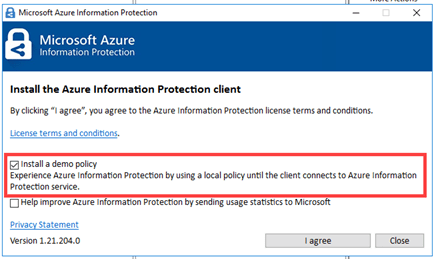
Once downloaded, click to install. If needed you can install a ‘demo policy‘ as part of the setup, which can be used for testing, until the application is connected to your ‘Azure Information Protection‘ service instance. You need to launch a PowerShell window, so the commands to use it can be run. The first task is to setup the SQL database that will be used by the scanning tool. This is done by typing the following:
For a default instance: Install-AIPScanner -SqlServerInstance SQLSERVER
For a named instance: Install-AIPScanner -SqlServerInstance SQLSERVER\AIPSCANNER
For SQL Server Express: Install-AIPScanner -SqlServerInstance SQLSERVER\SQLEXPRESS
We will use the SQL Express but you could use a full-blown SQL implementation if that is installed on your network. Firstly, however, you may need to import the ‘AIP‘ DLL for the commands to work.

Next, we can run the installation command:

When prompted type the service account you wish to use for the scanner.
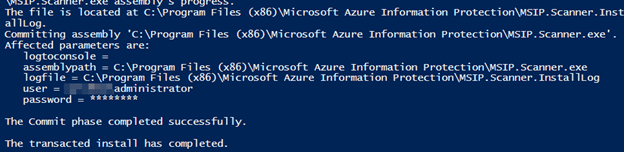
Once it has completed successfully you can check in the ‘Services‘ console and the new service will be listed.
Within the PowerShell console, we need to run the command that checks the status and mode of the scanner.

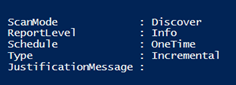
The scanner by default is set to ‘Discover’ mode, and outputting informational reports only. These settings can be changed easily by using the ‘Set-AIPScannerConfiguration‘ command.
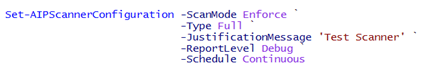
You need to set the repository of data that you wish to scan. Check what is being used by typing ‘Get-AIPScannerRespository‘. The first time you run this, it will be blank as nothing has been set. For this example, I am going to use a network share on a server. To set this we can use the following command:
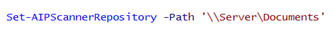
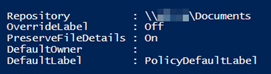
As part of setting the repository, you can also set some options that determine the configuration of the default label to apply.
Now, you need to get an ‘Azure Information Protection‘ authentication token for the scanner. This is done using the ‘Set-AIPAuthentication‘ command. When prompted login with your Office 365/Azure AD account that has access to your ‘Azure Information Protection‘ service. Once completed this will return an access token that will then be used by the scanner.

Open the ‘Services‘ console and start the service ‘Azure Information Protection Scanner‘. When this completes the scanner, service will stop automatically. Any reports, that were generated are stored within ‘%localappdata%\Microsoft\MSIP\Scanner\Reports‘ and have a ‘CSV‘ file extension.
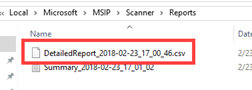
‘CSV‘ to review the files found, the label applied, and the condition used and found on the content. Of course, for this example, it was only set to ‘Discover‘ not ‘Enforce‘ which would have applied the labels and protections.
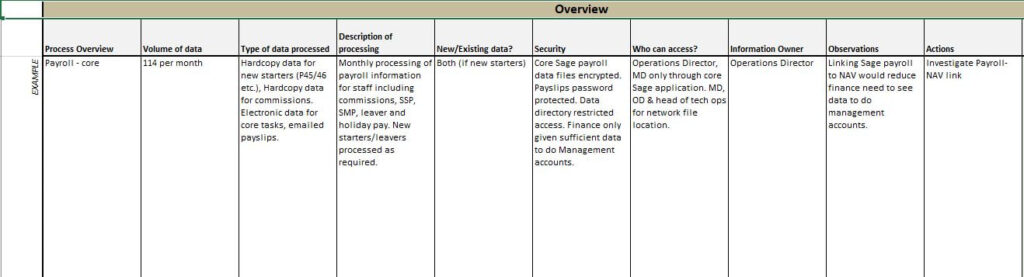
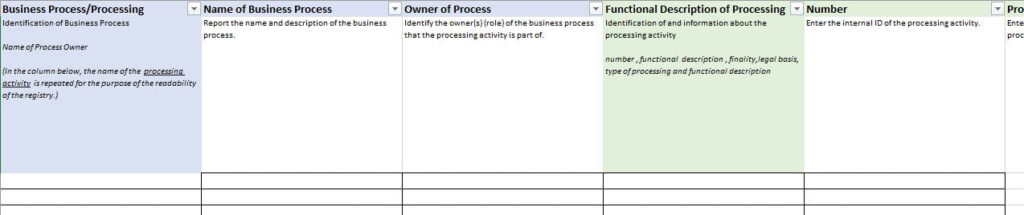
GDPR Templates

Thank you for a good overview of a subject many of our clients know little about. This is a great resource that I will be pointing them to!
You are most welcome Harald 🙂
Heello nice blog
Loved reading this thanks