In order to setup Azure MFA as Primary Authentication with ADFS, this does require you to move to Azure MFA (cloud-based version). I have not deployed Azure Multi-Factor Authentication Server (on-prem/hybrid version) in a few years for anyone as pretty much everyone I work with has moved on to cloud-based Azure MFA. Feature parity is pretty close to the same at this point and in my opinion, the days of Azure MFA Server on-prem are numbered. If you’re still on the on-prem Azure MFA Server, it is very easy to migrate to the cloud-based Azure MFA. I’m going to assume you have a working ADFS environment already that is federated with Azure AD using Azure AD Connect for this blogpost for a step by step guide.
Configure ADFS and Azure MFA to work
- Log into your ADFS server. In my example, I am using ADFS 4.0 with a Farm Behavior Level (FBL) set to 3 which means Windows Server 2016 and an Active Directory 2016 schema. You can always run the PowerShell cmdlet “Get-AdfsFarmInformation” on your ADFS server to show your FBL version. Go ahead and open the AD FS console:
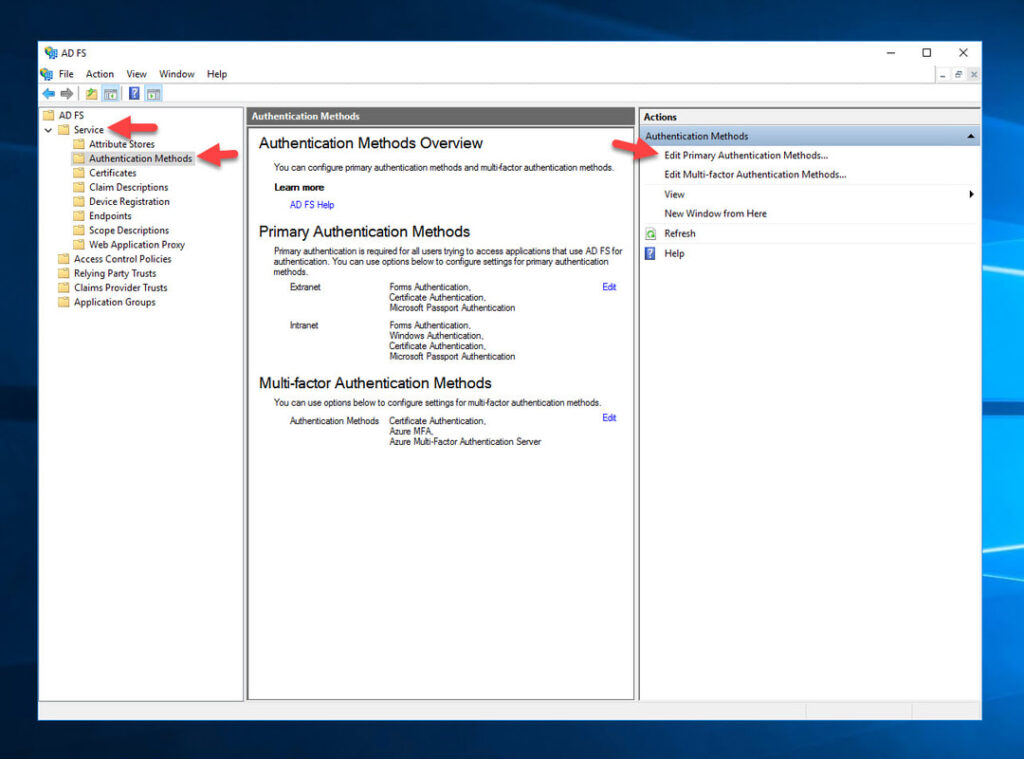
2. Click ADFS > Service > Authentication Methods > Edit Primary Authentication Methods
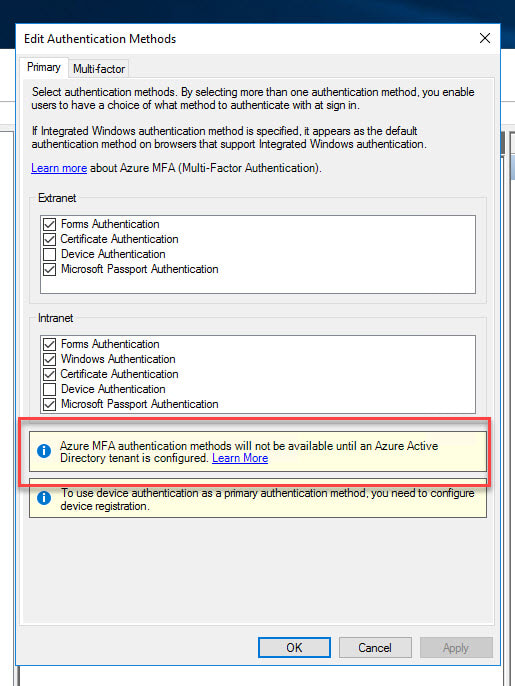
- You’ll notice for primary authentication there is currently no option for Azure MFA. There will be a notice asking you to integrate with an Azure AD tenant in order to use Azure MFA. Again, remember this is not the Azure MFA Server from on-prem which is usually configured on the Multi-factor tab. This is the cloud-based Azure MFA which means ADFS needs to talk directly to your Azure tenant and Azure AD to invoke Azure MFA:
- Log into your Azure tenant using Login-AzAccount PwerShell and copy out your Tenant ID.
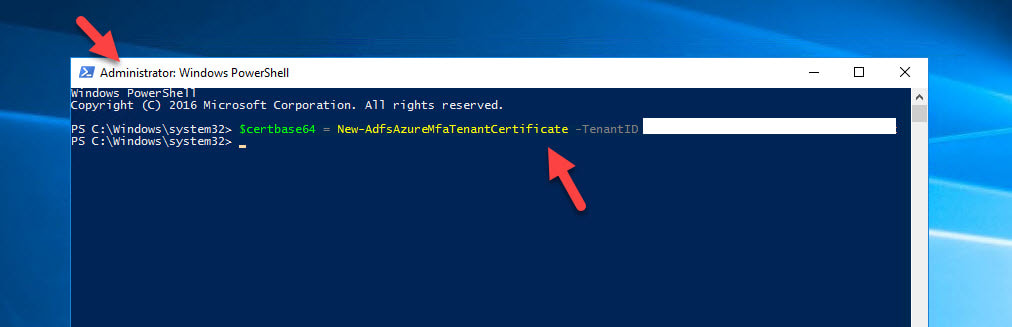
- On your AD FS server, open up an Administrator PowerShell window and type the below command to generate a tenant certificate to use with Azure MFA: $certbase64 = New-AdfsAzureMfaTenantCertificate -TenantID
$certbase64 = New-AdfsAzureMfaTenantCertificate -TenantID
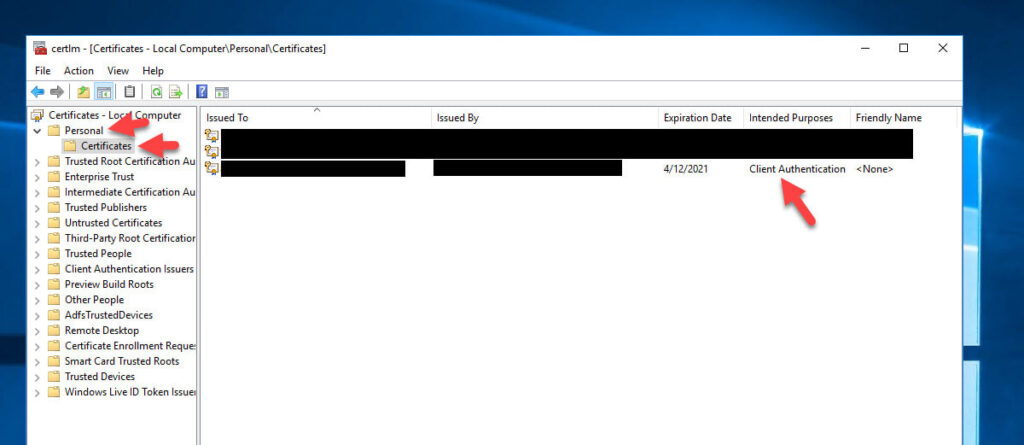
- This cert needs to be generated in each ADFS server in your farm. You can open up the Certificates console and see it is stored under Local Computer > Personal > Certificates as a Client Authentication certificate. Note that the default expiration date is 2 years from the date you generate it so be mindful that you need to renew this and include it in your ADFS certificate maintenance plans.
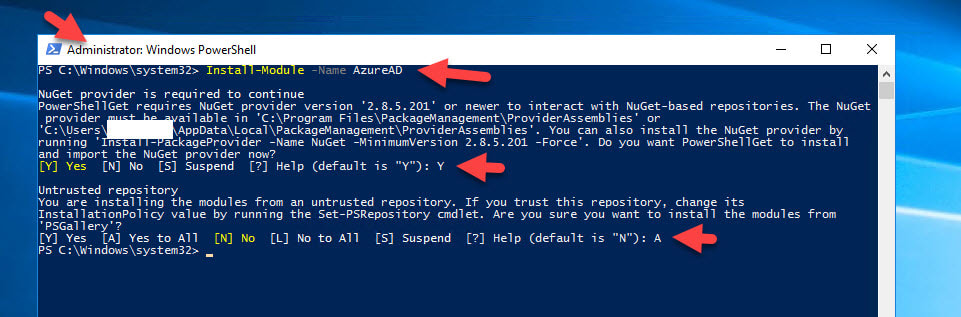
- Now you need to enable the ADFS servers to communicate with the Azure Multi-Factor Auth Client already registered in your Azure AD. The cert you just generated will be used as credentials to the Service Principal for the Azure Multi-Factor Auth Client. In your Administrator PowerShell window, type: Install-Module -Name AzureAD
Install-Module -Name AzureAD
and accept the prompt to get the Microsoft Online Services module installed.
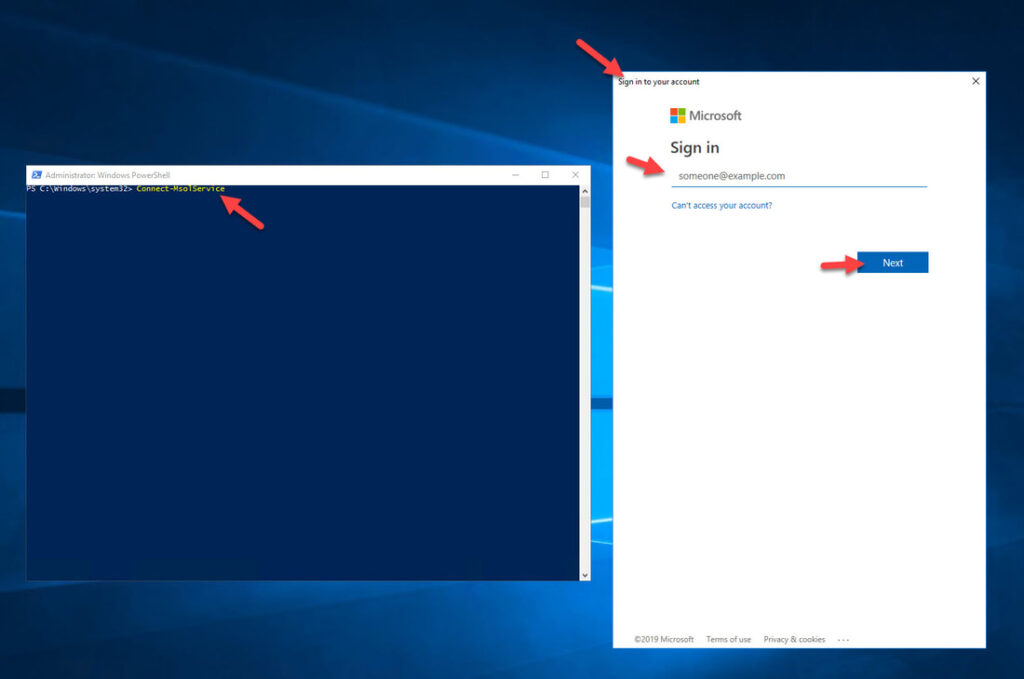
9. Now type: Connect-MsolService
Connect-MsolService
and a web view will open up asking you to sign-in to Azure. I typically use a global admin account here:
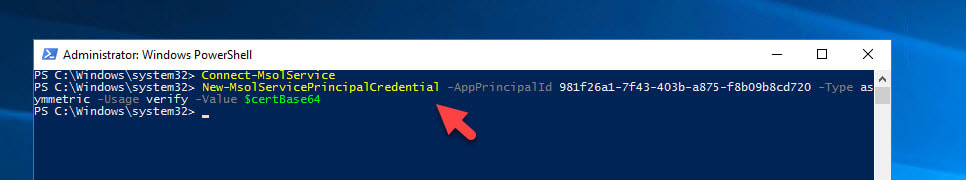
10. Once authenticated, we need to set the Service Principal to use the new cert with Azure MFA. Type in:
New-MsolServicePrincipalCredential -AppPrincipalId 981f26a1-7f43-403b-a875-f8b09b8cd720 -Type asymmetric -Usage verify -Value $certBase64
New-MsolServicePrincipalCredential -AppPrincipalId 981f26a1-7f43-403b-a875-f8b09b8cd720 -Type asymmetric -Usage verify -Value $certBase64
11. Now the next step is where we tell AD FS to use your Azure AD tenant with Azure MFA. You only need to run this from one of your AD FS servers since all servers will see this config change:
Set-AdfsAzureMfaTenant -TenantId <YourTenantID> -ClientId 981f26a1-7f43-403b-a875-f8b09b8cd720
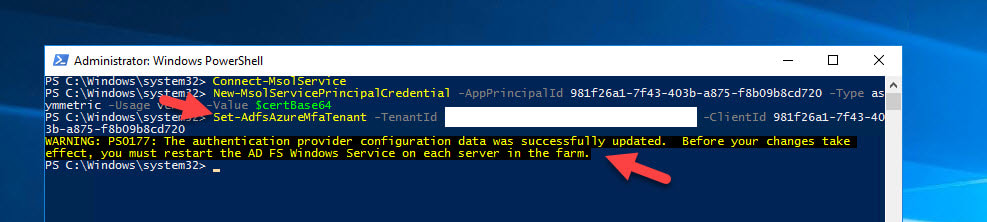
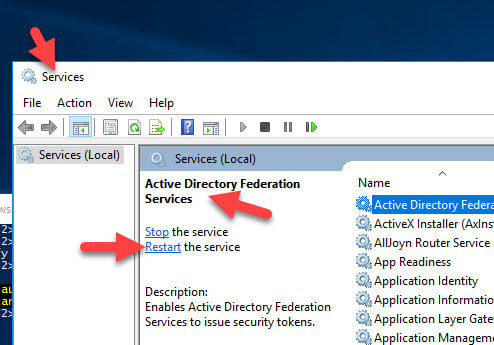
Now go into Services on each of your AD FS servers and restart the “Active Directory Federation Services” service.
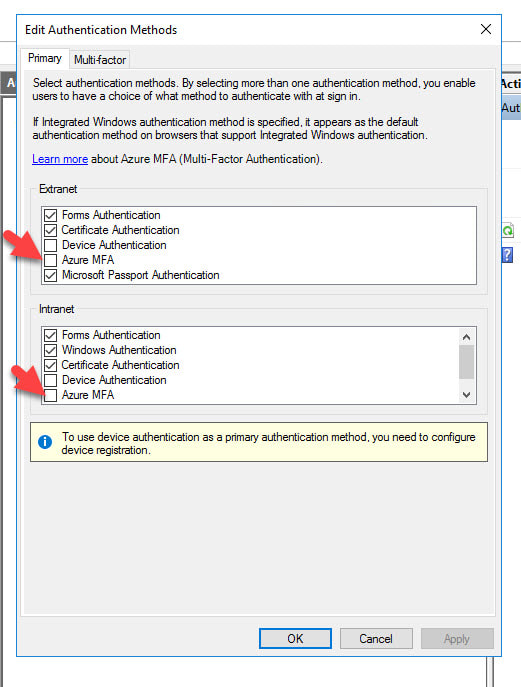
13. Close any ADFS MMC consoles you have open and then re-open and go to Edit Authentication Methods again. Now you will see a new Primary authentication option of Azure MFA for use with both your Extranet and Intranet!
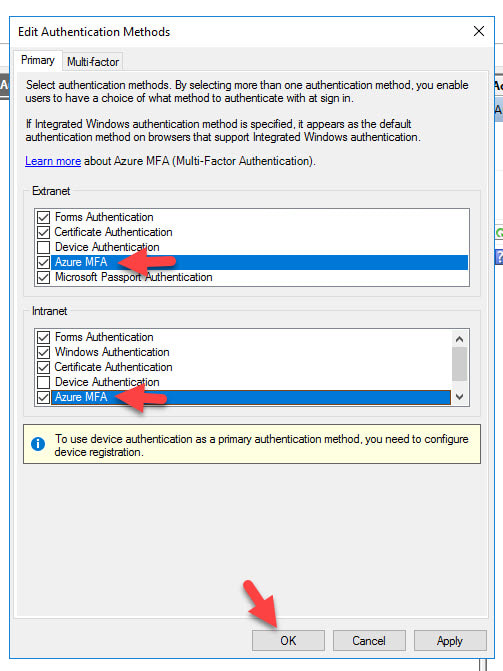
- Go ahead and check the box next to them so you can choose when the Azure MFA option is shown to users. Most companies choose to only enable it for their Extranet, meaning users that come in through the AD FS WAP (Web Application Proxy) servers in the DMZ. I’m just going to select both in this example since I will be testing logins from an internal Windows 10 desktop in the next few steps and I want to see the Azure MFA option show up:
The AD FS with Azure MFA as Primary Authentication user experience
- Now on my Windows 10 desktop, I am going to navigate to the IdP initiated AD FS login URL to test this. You’ll also probably want to disable Windows Authentication (IWA aka Integrated Windows Authentication) on the Intranet in AD FS if this a test environment just so you don’t get auto-logged in. Go to:
https://yourADFSsubdomain.yourcompany.com/adfs/ls/IdpInitiatedSignOn.aspx
https://yourADFSsubdomain.yourcompany.com/adfs/ls/IdpInitiatedSignOn.aspx
Hit the “Sign in to this site” radio button and then click Sign in.

Activity ID: bd15ad39-ca54-407f-4200-0080000000d5
Relying party: fs.pro.eg
Error details: Exception calling SAS.
Node name: 78c45cda-95d8-4aad-ae11-b1aadbfd3d74
Error time: Sat, 09 Oct 2021 09:31:14 GMT
i got that error after i already followed the same steps on your article and MS Docs
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/operations/configure-ad-fs-and-azure-mfa
This is Because TLS & .net Frame work are not using TLS 1.2 Please enable and for TLS1.2